CS2 Malware Announcement
Published: 2024-11-03
ExoTickler
Big thanks to everyone in the John Hammond discord server for helping and contributing!
UPDATE!!!
04/11
We’ve discovered it persists in people’s Exodus wallets by using DLL Search-order hijacking.
This DLL will be at %LOCALAPPDATA%\exodus\app-24.41.6\profapi.dll, or a similar app- directory.
To remove the persistence, remove this file
Thanks to jh discord dudes again for finding this!
What we know
Key Points
- The malware is an Exodus Wallet Stealer, which we are calling ExoTickler.
- If you don’t have Exodus Wallet you are not effected.
- The claims from others that this “Digs into your BIOS”, “Injects your macros”, “Sideloads stuff”, “Hijacks this”, “Detonates that”, or similar claims are false.
- Windows Defender has added a signature for this malware (
Trojan:Win32/Shelood)
Attack Chain
- The DllMain function in FastMath.dll is run.
- FastMath.dll extracts, decrypts and executes a second stage.
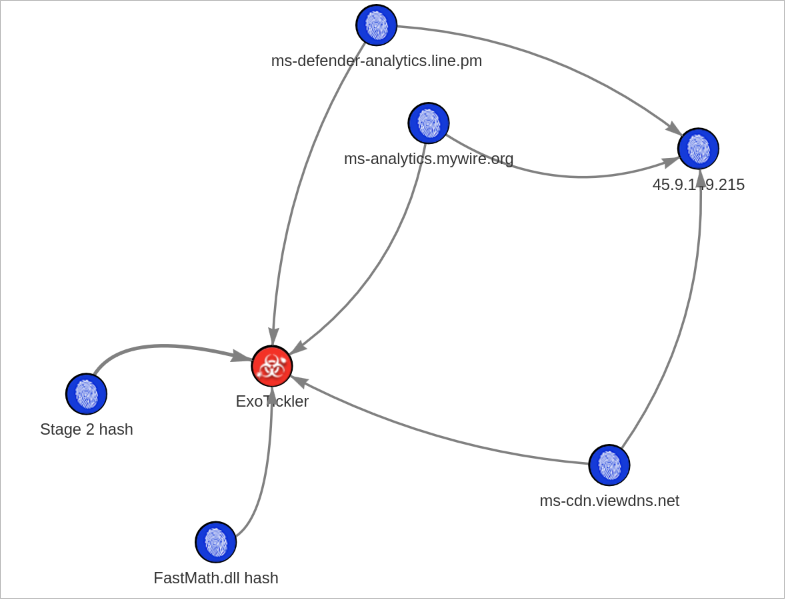
- Stage 2 steals your Exodus Wallet seed phrase and exfiltrates it to the following IP via 3 domains, one of which is defunct.
Indicators of Compromise (IoCs) - also available in STIX format (WIP, SOON)
hxxps://pricing[.]a[.]exodus[.]io/ticker- not generally malicious, but the stage 2 payload interacts with this API45[.]9[.]149[.]215- c2 ipms-defender-analytics[.]line[.]pm- c2 domainms-analytics[.]mywire[.]org- c2 domainms-cdn[.]viewdns[.]net- c2 domain8c6c3f9b3fd8497322cd9e798790aa3485a44f9c5418bb4aa97b630a3fb8cead- sha256 of FastMath.dll671c26b7d17db3af70f7ad24e48cf9eabdbac68a9604fa1b803608cff8a5df79- sha256 of stage 2 (for reference, will not appear in memory or on-disk)
Other resources
- https://www.virustotal.com/gui/file/8c6c3f9b3fd8497322cd9e798790aa3485a44f9c5418bb4aa97b630a3fb8cead/details
- https://tria.ge/241102-21qhqs1lgj - note: other behavioural analysis runs of this have been incorrectly marked as malicious as the person tried to download directX, or other malware from chrome inside the sandbox.
What you need to do if you think you were infected
- Uninstall CS2, as well as the modpack.
- Reinstall CS2.
- Remove the malicious
profapi.dllDLL inside the exodus app folder e.g.%LOCALAPPDATA%\exodus\app-24.41.6\profapi.dll - If you are willing to accept the risk, reinstall the latest version of the modpack.
FAQ
I play CS2. I use this mod. Am I effected?
For this, I would follow the official advice from the CS2 forum post:
- If you have played using the affected version, please check your local files. If you have any malicious files installed, you will find them here; %localappdata%lowColossal OrderCities Skylines II.cacheModsmods_subscribed inside the folder 80095_13.
- Note that it is only **specifically the 80095_13 folder** that will contain malicious files; if you do not see this folder, you do not have the compromised version of the mod.Are my external drives effected?
No, not that we know of.
Was it targeting any other cryptocurrency wallets?
No, not that we know of. The only activity we saw targeted Exodus (specifically, it tries to read %s\AppData\Roaming\Exodus\exodus.wallet\seed.seco).